For ops leaders, the decision is about risk, cost structure, control, and long-term flexibility. A PBX system sits at the center of customer communication. Changing it affects uptime, compliance processes, reporting visibility, and team scalability.
This guide breaks down cloud PBX vs on-premises PBX from an operational perspective. We’ll examine infrastructure responsibility, five-year cost exposure, scalability limits, compliance considerations, and industry-specific realities. This way, you can determine which model aligns with your business structure.
Cloud PBX vs on-premises PBX: the architectural difference that really matters
Most think the difference between cloud PBX vs on-premises PBX is where the server sits. But we’re here to tell you it’s actually who carries operational responsibility.
At an architectural level, the decision determines who owns the infrastructure, who maintains it, and who absorbs risk when something fails.
Infrastructure ownership vs infrastructure responsibility
With an on-premises PBX, your company owns the hardware and typically manages the supporting infrastructure. That includes physical servers, session border controllers, power redundancy, and network configuration. Internal IT teams are responsible for updates, security patches, firmware upgrades, and failover setup.
With a cloud PBX, infrastructure is hosted and maintained by the provider. The provider handles system updates, patch management, platform-level maintenance, and core redundancy architecture. Your team manages configuration, routing logic, and operational workflows inside the platform.
The operational burden shifts in three critical areas:
Updates and upgrades: On-premises systems require scheduled upgrades. These may involve maintenance windows, compatibility testing, and potential hardware refresh cycles. Cloud-based platforms apply updates centrally, reducing internal upgrade coordination.
Failover and redundancy: On-premises resilience depends on how well redundancy is architected. Secondary servers, backup power, and secondary ISPs must be provisioned and maintained internally. In a cloud model, redundancy is built into the provider’s infrastructure. Business continuity depends more on internet connectivity than local hardware.
Security patching: With on-site systems, patching cadence depends on internal IT capacity and governance. Delays increase exposure risk. Cloud providers manage patch deployment at the infrastructure level, while customers retain responsibility for access controls and user management.
The real distinction becomes visible during outages.
If a power failure, hardware fault, or misconfiguration affects an on-premises system, resolution falls to internal teams or contracted telecom specialists. Recovery time depends on internal expertise and spare hardware availability.
In a cloud environment, incident response at the infrastructure layer is handled by the provider.
This doesn’t eliminate operational responsibility on the customer side. Teams still manage routing logic, queue configuration, and user access. But infrastructure-level recovery doesn’t depend on internal telecom engineering resources.
The architectural question is therefore practical: Do you want to own telephony infrastructure, or do you want to manage telephony operations?
Control layers: physical, network, application
“More control” is often cited in discussions about on-premises systems. The term is rarely defined. Control exists in layers.
Hardware control: On-premises PBX provides direct control over physical servers and telephony equipment. You decide hardware specifications, physical access policies, and replacement cycles. In a cloud model, hardware control sits with the provider.
However, hardware ownership alone doesn’t guarantee better performance or stronger security. It simply shifts responsibility.
Network control: On-site systems allow tighter integration with internal network architecture, including VLAN configuration and firewall rules. In a cloud environment, network reliability depends on ISP quality and bandwidth provisioning, while the provider manages infrastructure beyond the public internet edge.
Application-level control: Both models provide application-level configuration, but the mechanisms differ.
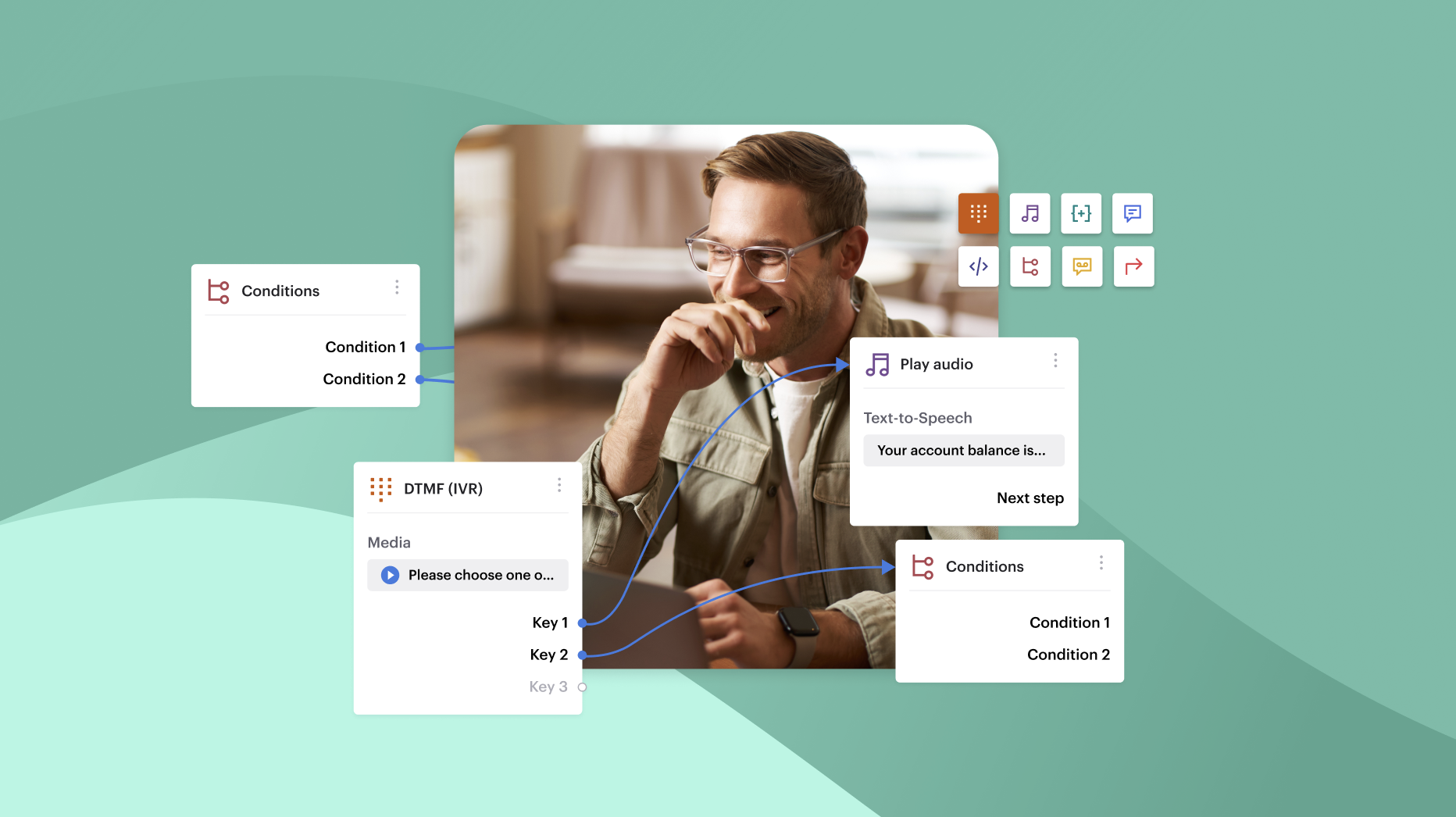
Modern cloud contact center platforms provide rule-based routing logic, IVR paths, queue management, and conditional flows through flow builder tools. These flows are predefined and structured, allowing teams to configure decision trees without direct infrastructure changes.
This is application control, not infrastructure control. It allows operational customization without managing servers.
On-premises systems may allow deeper system-level configuration, but changes often require specialized telecom expertise.
Data control: With on-premises PBX, call recordings and logs are typically stored on internal infrastructure unless external storage is configured. With cloud platforms, recordings and call data are stored within the provider’s infrastructure, while access is governed by user permissions and platform controls.
Control at this layer depends less on physical ownership and more on governance structure: who can access recordings, who can export logs, and how visibility is managed internally.
The architectural trade-off is therefore layered:
- On-premises maximizes hardware-level control but increases operational responsibility.
- Cloud models centralize infrastructure responsibility while preserving operational configuration control through platform-level tools.
The decision should be based on internal capability and risk tolerance, not on the assumption that physical ownership automatically equals stronger control.
True cost comparison: CapEx vs OpEx over 5 years
Most comparisons between cloud PBX vs on-premises PBX stop at “high upfront cost vs monthly subscription.” That framing is incomplete.
The real question is total cost exposure over a five-year period. That includes infrastructure, staffing, downtime risk, and upgrade cycles.
Upfront infrastructure and licensing costs
With an on-premises PBX, initial costs extend beyond the PBX software license.
Typical capital expenses include:
- Server hardware (primary and backup systems)
- Redundancy equipment for failover
- Session Border Controllers (SBCs)
- Rack space and network equipment
- Implementation and configuration services
Industry research from firms such as Deloitte and Gartner consistently shows that telecom infrastructure projects often exceed initial hardware estimates once redundancy, integration, and deployment services are included.
In addition, internal IT staffing must be factored into the equation. Even if no new hires are required, telecom infrastructure consumes engineering time. That cost is rarely isolated in budgeting discussions.
Upgrade cycles add another layer. Most on-premises telephony systems require major upgrades or hardware refreshes every five to seven years. That introduces another capital event, not just software updates.
By contrast, cloud platforms do not require hardware procurement or infrastructure installation. The cost model shifts from capital expenditure (CapEx) to operating expenditure (OpEx).
However, lower upfront cost does not automatically mean lower total cost. It means the cost structure changes.
Ongoing operational costs you might underestimate
The ongoing costs of on-premises systems are often less visible but materially significant.
Maintenance contracts: Vendors typically require annual support and maintenance agreements. These can represent a meaningful percentage of the original system cost.
Downtime exposure: Unplanned outages are expensive. Gartner has estimated the average cost of IT downtime at thousands of dollars per minute, with figures often cited around $5,000–$6,000 per minute depending on industry and scale. While not every organization experiences losses at that level, the financial impact of prolonged telephony downtime can be substantial.
With on-site systems, recovery time depends on internal expertise and hardware availability. If a critical component fails, resolution may require vendor coordination and physical replacement.
IT personnel allocation: Telephony infrastructure requires monitoring, patching, configuration changes, and troubleshooting. Even if handled by existing staff, this represents opportunity cost. Those hours are not spent on revenue-generating or strategic initiatives.
Power and cooling: Server rooms require electricity, backup power solutions, and environmental control. These costs are incremental but real, particularly for organizations operating multiple sites.
Cloud-based systems shift most infrastructure-level operational costs to the provider. Internal teams focus on configuration, routing, reporting, and workflow management rather than hardware maintenance.
Cloud PBX advantages in cost predictability
One of the primary cloud PBX advantages is cost predictability.
Instead of large capital outlays followed by irregular upgrade investments, organizations operate on a recurring usage-based pricing model.
This has three practical implications:
Usage-based pricing: Costs scale with the number of users, call volume, and selected capabilities. Many mid-sized organizations, particularly in industries like Fintech and outsourced telemarketing, prefer this structure because it aligns expenses with revenue-generating activity.
Elastic scalability: Adding or reducing agents does not require hardware procurement. This is particularly relevant for BPOs and outbound teams with fluctuating demand.
No hardware refresh cycles: There is no five-year infrastructure replacement event. Platform updates and infrastructure maintenance occur at the provider level.
That doesn’t mean cloud models are automatically cheaper over five years. In high-scale, highly stable environments with strong internal IT capabilities, on-premises systems may amortize differently.
The key distinction is financial flexibility.
On-premises PBX concentrates risk and investment upfront.
Cloud PBX distributes cost over time and aligns it with operational scale.
The right choice depends on capital tolerance, growth volatility, and internal technical capacity.
Scalability and growth: what happens when you add 100 agents?
Growth exposes architectural limits.
Adding 5 users is simple in almost any system. Adding 100 agents in a quarter is where infrastructure design starts to matter.
Scaling on-premises infrastructure
With an on-premises PBX, scaling depends on physical and licensing capacity.
Three constraints usually appear:
Hardware procurement lead times: If current servers are near capacity, expansion may require new hardware. That means vendor sourcing, shipping timelines, installation, and configuration. In many cases, this is measured in weeks, not days.
Licensing limits: On-prem systems are often licensed by concurrent users or ports. If capacity ceilings are reached, additional licenses must be purchased and sometimes activated through vendor intervention.
Physical space and infrastructure constraints: Additional servers require rack space, power availability, and cooling capacity. If redundancy is required, expansion costs double.
Let’s model a practical scenario.
A Fintech firm operates with 200 brokers running outbound sales. Growth projections require scaling to 350 brokers within six months.
Under an on-prem model, leadership must ask:
- Is current hardware sized for that capacity?
- Is network bandwidth sufficient?
- Are additional SBCs required?
- Does IT have implementation bandwidth?
- Will failover architecture scale proportionally?
If the answer to any of these is no, expansion becomes a project instead of another operational decision.
That doesn’t make on-premises wrong. But it makes scaling dependent on capital planning and infrastructure timelines.
Scaling cloud phone systems for businesses
With cloud phone systems for businesses, scaling shifts from infrastructure expansion to account configuration.
Seat provisioning typically involves:
- Creating new user accounts
- Assigning numbers or extensions
- Placing agents into queues
- Configuring routing logic
There is no hardware procurement cycle.
This becomes particularly relevant for distributed and outbound-heavy teams.
Geographic expansion: If a Fintech company opens a new sales hub in another country, agents can operate through internet connectivity without deploying telephony hardware locally. Tools like the Voiso Mobile App allow agents to handle calls securely from supported mobile environments while remaining visible in centralized dashboards.
Local caller IDs: Outbound teams often require local presence dialing to improve answer rates. Cloud architectures allow assignment of local numbers without physical deployment in each region, subject to regulatory availability.
Global routing: Inbound calls can be routed using predefined, rule-based logic such as country, queue, or skill group. Routing logic is configured at the application level rather than through hardware changes.
Outbound efficiency at scale: For outbound-driven teams such as Fintech brokers, BPOs, or microlenders, Answering Machine Detection (AMD) can identify machine-answered calls with high accuracy before connecting them to agents.
This doesn’t eliminate scaling considerations. Internet capacity, workforce onboarding, and operational supervision still matter.
But infrastructure scaling becomes configuration-driven rather than hardware-driven.
Compliance, security, and regulatory risk
For many organizations, this is the deciding factor in the cloud PBX vs on-premises PBX discussion.
Fintech firms, microlenders, BPOs serving regulated industries, and financial services teams all operate under strict communication requirements. The risk is not theoretical. It is operational.
The real question is not “Which model is secure?”
It’s: Where does responsibility sit, and how is it enforced?
Data sovereignty and call recording requirements
Most regulated industries must address three areas:
- PCI DSS for handling payment data
- GDPR for personal data protection
- Financial communication recording requirements for audit and dispute resolution
Both cloud and on-premises systems can support structured compliance processes. The difference lies in governance and operational control.
Call recording controls: Some regulations require pausing recordings when sensitive data is shared.
Call review and monitoring: Supervisors in regulated environments often need structured visibility into conversations. Voiso’s AI Speech Analytics generates transcripts, keyword tracking, and conversation scores after calls are completed.
This supports oversight. It doesn’t replace formal compliance review processes.
Now consider the infrastructure layer.
In an on-premises model:
- Your organization manages storage location.
- Your IT team controls encryption configuration.
- Your team is responsible for patching vulnerabilities.
- Your organization coordinates breach response.
In a cloud model:
- The provider manages infrastructure-level encryption and patching.
- Data is stored within the provider’s environment.
- Incident response at the infrastructure level is handled by the provider.
- Your organization still manages user access, retention policies, and internal governance.
The compliance difference is accountability.
Before choosing either model, leadership should ask:
- Who audits the infrastructure?
- Who verifies encryption standards?
- Who manages vulnerability patching timelines?
- Who owns breach notification procedures?
Those answers determine risk exposure more than deployment type alone.
Security myth: is On-Premises actually safer?
It’s common to assume that on-premises equals more secure because the hardware is physically owned.
That assumption deserves scrutiny.
Security failures often result from:
- Delayed patching
- Misconfigured firewalls
- Over-permissioned user accounts
- Lack of monitoring
Mid-sized organizations rarely maintain dedicated telecom security teams. Telephony infrastructure is often one responsibility among many for IT departments.
Cloud providers, by contrast, operate centralized infrastructure and are subject to external audits.
Certification doesn’t eliminate risk. It indicates that processes and controls are audited against defined standards.
The core trade-off is this:
On-premises systems provide physical control, but security strength depends entirely on internal discipline and expertise.
Cloud systems centralize infrastructure security responsibilities, but organizations must trust external governance frameworks and maintain strict internal access control.
Neither model is inherently safer.
Security maturity, operational discipline, and clearly defined ownership determine the real outcome.
Performance, uptime, and business continuity
When telephony fails, revenue slows down immediately. Sales teams stop dialing. Support queues stall. Service levels drop.
The performance question in hosted PBX vs on-site PBX is about how many failure points exist, and how quickly you can recover.
Single point of failure risks in On-Site PBX
On-premises systems are physically tied to a location. That introduces concentrated risk.
Common failure points include:
Power outages: If the building loses power and backup systems fail or are insufficient, the PBX becomes unavailable. Even short outages can interrupt active calls.
Local ISP failure: If connectivity drops and there is no secondary provider configured correctly, inbound and outbound calling can stop entirely.
Hardware failure: Servers, storage devices, and SBCs have physical limits. If a critical component fails and no redundant hardware is immediately available, recovery depends on repair or replacement timelines.
Redundancy can absolutely be designed into on-site architecture. Secondary servers, backup lines, and failover logic can reduce risk. But each layer adds cost, complexity, and maintenance responsibility.
Business continuity, in this case, is only as strong as the internal architecture and the team maintaining it.
Distributed redundancy in Hosted PBX vs On-Site PBX
In a hosted PBX vs on-site PBX comparison, resilience is structured differently.
Cloud-based systems are typically built on distributed infrastructure across multiple data centers. If one data center experiences an issue, traffic can be routed through another location. This reduces dependency on a single physical site.
But, it doesn’t remove all risk. Internet connectivity at the customer’s location remains a dependency. If local internet access fails and no backup connection exists, agents may still be impacted.
However, the failure domain is different:
- On-site PBX concentrates infrastructure risk in one building.
- Hosted PBX distributes infrastructure risk across data centers.
Failover routing: Predefined, rule-based routing configurations can redirect calls if a queue or agent group is marked unavailable. This routing is rule-based and configured at the application level rather than through physical rewiring.
SLA-backed uptime: Hosted providers typically define response times and escalation paths within structured support agreements.
An SLA doesn’t prevent downtime. It defines how incidents are handled and how quickly support responds.
The practical question is this:
If your primary office becomes unavailable tomorrow, how long would your telephony system remain operational?
With on-site infrastructure, continuity depends on local resilience design.
With hosted infrastructure, continuity depends on distributed architecture and internet access.
Neither model eliminates risk. They distribute it differently.
Industry-specific recommendations
A PBX decision looks different depending on how you sell, how you support customers, and what regulators expect. Below are practical recommendations based on common operating models.
For fintech and regulated sales teams
Fintech sales teams tend to run high-volume outbound motions and operate under strict communication rules. The PBX choice needs to support controlled recording, structured review, and fast scaling without breaking governance.
What typically matters most
- Call recording for audits, disputes, and internal QA.
- Multilingual transcription so supervisors can review calls across markets. Voiso’s Speech Analytics supports transcription in multiple languages (the product materials list 10+ languages).
- High outbound efficiency, especially when brokers spend large portions of the day dialing.
- AMD to reduce voicemail exposure, so agents spend more time on live conversations. Voiso provides Answering Machine Detection designed to identify machine-answered calls quickly.
Recommendation:
- Cloud-first is often the practical default because it reduces infrastructure burden and speeds up onboarding across regions.
- If strict data localization rules apply (or your legal team requires in-country storage), a hybrid approach may be necessary. Treat this as a legal and governance decision, not just a technical one.
For BPOs and outsourced telemarketing firms
BPOs and telemarketing providers are built around elasticity. Headcount changes with client demand, campaigns ramp fast, and teams are often distributed across countries.
What typically matters most
- Scalability: add or remove agents without hardware projects.
- Local caller ID management to support outbound connectivity and reduce friction when dialing internationally.
- Automated dialing workflows and list processing discipline.
- Agent utilization tracking via dashboards and call outcome reporting.
Why on-prem often slows expansion: On-premises scaling tends to turn growth into a procurement cycle: more capacity means more hardware, more redundancy planning, more vendor coordination, and more time. That’s manageable in stable environments, but it clashes with campaign-driven ramp-ups and multi-country staffing models.
For OTAs and travel providers
Travel support is operationally messy: booking changes, supplier issues, and time-sensitive disruptions. Customers also switch channels constantly.
What typically matters most
- Omnichannel handling so agents can manage voice and messaging channels in one workspace and hand conversations across channels when needed. Voiso’s omnichannel materials list support for channels like WhatsApp and others, plus unified reporting across channels.
- SLA monitoring through real-time visibility into queues and response performance (Voiso shows SLA-focused monitoring and reporting concepts in its omnichannel workspace materials).
- International calls and distributed staffing, often across multiple time zones and regions.
Recommendation:
Cloud is usually the cleaner fit when your operation spans countries, seasonal staffing changes, or multiple support channels. On-prem can work for single-location operations, but it can become restrictive once you introduce 24/7 global support.
For microlenders and collections teams
Collections and loan servicing teams often blend outbound calling with follow-ups, while maintaining strict controls over what’s said and recorded.
What typically matters most
- Blended outreach (voice + SMS) to send payment links, reminders, or confirmation details after calls. Voiso supports SMS follow-up and templates in its materials.
- Compliance monitoring through structured call recordings and post-call review. Voiso Speech Analytics provides transcripts and searchable call details to support review workflows.
- Cost control through predictable staffing and operational reporting, especially when teams expand seasonally or by portfolio performance.
Trade-offs to call out:
- Cloud can simplify scaling collections teams quickly, but you must still implement strict access controls and retention policies internally.
- On-prem can offer more direct control over storage location, but it also puts patching, security hardening, and resilience fully on your team. If that team is small, risk can increase rather than decrease.
Hybrid PBX Models: when a mixed approach makes sense
The discussion around cloud PBX vs on-premises PBX is often framed as binary. In practice, some organizations operate in between.
A hybrid model combines elements of on-site infrastructure with cloud-based routing or remote agent access. It’s not automatically more advanced. It is usually the result of specific operational constraints.
Below are three situations where a mixed approach can make sense.
Scenario 1: Multi-site organizations with legacy infrastructure
A company may operate:
- A headquarters with an existing on-premises PBX
- Several regional offices or remote teams
Replacing the entire system at once may not be practical due to sunk infrastructure costs or contractual obligations.
In this case:
- HQ telephony may remain on-premises.
- Remote offices or new branches operate through a cloud contact center platform.
Routing logic can be configured so inbound calls are distributed across both environments based on predefined rules. Application-level routing tools can allow rule-based queue handling and call distribution without modifying physical wiring.
This allows gradual expansion without a full infrastructure replacement.
Scenario 2: gradual migration strategy
Some organizations want to reduce infrastructure ownership over time but can’t transition immediately.
A staged approach may look like:
- Keep core inbound lines on-premises.
- Move outbound sales or support teams to cloud-based infrastructure.
- Shift routing logic progressively as contracts expire or hardware reaches end of life.
This reduces migration risk and avoids a single cutover event that could disrupt operations.
Hybrid models in this context are transitional. They allow teams to test cloud workflows while maintaining continuity in legacy systems.
Scenario 3: HQ On-Premises with remote or distributed agents
In regulated industries, headquarters may maintain on-site storage or specific infrastructure controls. At the same time, sales teams, BPO contractors, or seasonal agents may work remotely.
A hybrid structure can allow:
- Core telephony control to remain in a central location.
- Remote agents to connect via cloud-based access points.
Routing decisions remain rule-based and centrally configured. Flow Builder enables rule-based conditional routing between queues and agent groups.
This avoids deploying physical hardware in every remote location.
Decision framework: how to choose between Cloud PBX and On-Premises PBX
If you’re asking, “How do I choose between cloud PBX and on-premises PBX for my company?”, the answer is rarely about features.
It’s about financial structure, internal capability, growth plans, and risk tolerance.
Below is a simplified decision matrix to clarify the trade-offs.
Decision matrix
| Decision Factor | Cloud PBX | On-Premises PBX |
| CapEx tolerance | Low | High |
| IT team size | Small | Large |
| Geographic expansion | Easy | Complex |
| Compliance customization | Strong (platform-level controls) | Very high (full infrastructure control) |
| Hardware control | No | Yes |
| Upgrade cycles | Automatic (provider-managed) | Manual (internal responsibility) |
This table doesn’t imply one model is superior. It shows where operational responsibility sits.
Cloud centralizes infrastructure management.
On-premises centralizes infrastructure ownership.
5 critical questions to answer before deciding
Before selecting either model, leadership teams should answer these questions clearly.
- What is your 3-year growth plan?
If you expect rapid hiring, new markets, or seasonal scaling, infrastructure flexibility becomes critical. If headcount is stable and centralized, long-term amortization may matter more. - How much downtime can you afford per hour?
Estimate the financial impact of telephony interruption. Then evaluate whether your internal team can design and maintain redundancy at that level. - Do you have in-house telecom engineers?
Owning infrastructure requires active management. If telecom expertise is limited, operational risk increases in an on-premises model. - Are you expanding internationally?
Global expansion increases routing complexity, local number management, and staffing distribution. Cloud models typically simplify this structurally. - Do you require custom telephony hardware integrations?
If your environment depends on specialized on-site integrations or legacy systems that cannot be abstracted into software-based routing, on-premises or hybrid may be necessary.
Final verdict: there is no universal winner
There is no permanent winner in the cloud PBX vs on-premises PBX debate.
The right choice depends on organizational maturity, internal capability, and long-term strategy.
Early-stage companies typically benefit from cloud infrastructure. Capital is preserved, setup is faster, and internal IT overhead remains low. The focus stays on customer acquisition and operational execution rather than infrastructure management.
Growth-stage companies often lean the same way. When headcount expands quickly, when teams become distributed, or when new markets open, flexibility matters more than hardware ownership. Scaling through configuration is usually simpler than scaling through procurement.
Highly regulated enterprises with established IT departments may choose differently. If they maintain dedicated telecom engineers, strict data governance policies, and structured infrastructure oversight, on-premises or a hybrid model, can align with internal controls and long-term amortization strategies.
The decision should be framed as infrastructure ownership vs operational agility.
Before committing, evaluate:
- How stable is your organizational structure?
- How much infrastructure do you want to manage directly?
- How fast do you expect your communication model to evolve?
Choose the model that supports your next stage, not where you’re currently at.
Explore how Voiso’s cloud contact center adapts to different operating models and growth patterns.